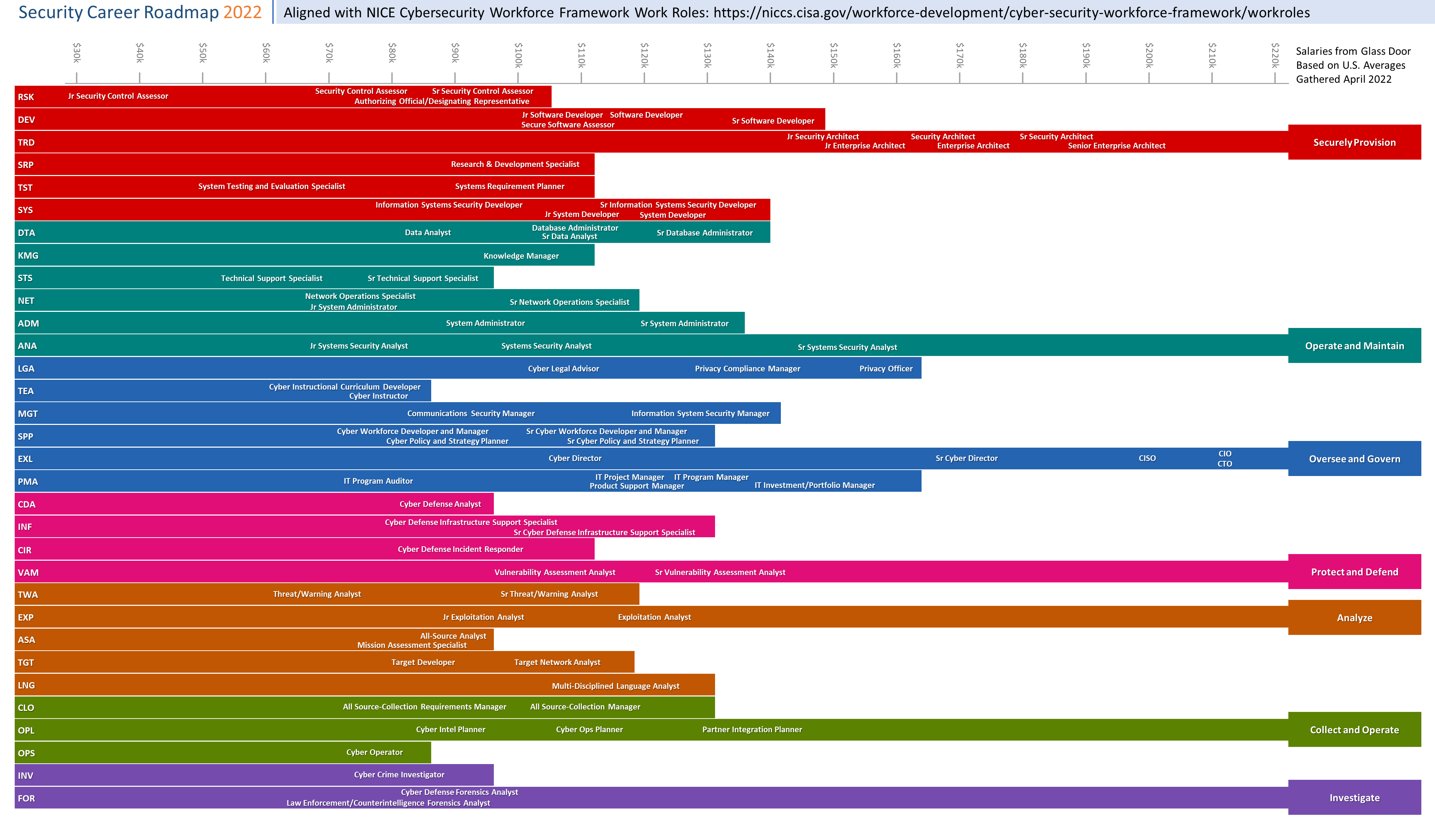
Getting Started in Cybersecurity
Introduction
If you’re reading this, then first I should say: welcome to the community!
Trying to figure out where to get started when considering a career in cybersecurity can be hard, but it doesn’t have to be. From the onset, there are three things you want to focus on early in your cybersecurity career:
Develop your core disciplines in Information Technology (IT) and/or Computer Science (CS). These subjects were where cybersecurity as a domain were born from. The more technical, granular aspects of cybersecurity continue to stem from (and build upon) an understanding of these subjects (e.g. programming, networking, systems, etc.). This is typically accomplished through things like enrolling in university or checking out Massive Open Online Courses (MOOCs) such as EdX, Coursera, Udemy, etc.
Explore the diversity of career paths and jobs that exist within the industry. It’s easy to become overwhelmed when starting out in cybersecurity. By learning about what professions exist, you can develop an understanding of what kinds of requirements, skills, certifications, and trainings you need to pursue in order to become who you want to be. This means speaking with existing professionals, listening to industry-related podcasts, attending conferences, and reading up on what other people do.
Improve your employability. Although the U.S. Bureau of Labor Statistics says that there is going to be enormous growth in available cybersecurity positions and there remains a reported shortage of qualified laborers, it is still challenging to land your first job. While it’s certainly possible to directly land a job in cybersecurity absent any other qualifications, the job hunt is certainly made easier by having experience in related fields (such as network engineering, software development, etc.). Either way, a plan and deliberate efforts towards putting your best self forward helps considerably. This manifests in all kinds of ways, including pursuing relevant certifications, taking on cyber-adjacent lines of work (if not cyber work directly), building a homelab, fostering a professional network, etc.
The remainder of this article goes into greater detail of the above-named actions.
Developing Your Disciplines
Without a doubt, failing to comprehend the fundamentals of IT and CompSci will hurt your entry into many roles within cybersecurity (and all that are engineering-centric). Granted, there exists plenty of work that won’t necessarily require you to know particular skills like coding (Risk Assessments and Policy Management as an example), but ask yourself: “How can I protect something if the threats to it know more than I do?” Or, more pragmatically speaking: “Who will hire me if I don’t know the basics?”. Popular approaches towards developing underlying competencies include:
- University
- Military service
- Cyber-adjacent employment
University
One option people consider when entering the field is enrolling as a student into a degree-granting program. There are a number of benefits conferred to the college-bound, including:
- Access to the protected class of employment known as internships (which fosters a work history directly within the industry).
- Structured learning environments and knowledgeable staff who you can engage.
- An environment rich with research in interesting emergent areas.
- An opportunity to observe the intersection of multi-disciplinary areas with the domain (e.g. AI/ML, Law, Psychology, etc.), which is more exceptional outside of academia.
If uncertain about the kind of subject-matter to study at the undergraduate-level, I typically encourage Computer Science programs vs. Cybersecurity offerings.
This decision is not without its controversies however, as many professionals within cybersecurity can either point to themselves or someone they know who has worked their respective career without attaining a degree within the disciplines of IT, CompSci, or the like. This also doesn’t begin to address the cost of these program, which can be extraordinary (especially for career-changers who may already have debt from earlier unrelated studies).
Military Service
For those both willing and able, military service can be an excellent way for launching your career in cybersecurity. For U.S. servicemembers regardless of occupational specialty, the military provides a security clearance (which transitions well to other agencies, such as the NSA, as well as contractor-work, such as with Northrop Grumman). For those aligned to cybersecurity, your training also is generally inclusive of commonly sought certifications, if not opportunities to pursue said certifications. You also foster a pertinent work history in that time, which is one of the most compelling features of a job application. There’s also a multitude of benefits afforded to military veterans, including the GI Bill, which makes a university education way more accessible. Finally, some of the most engaging and real-world impacts in cybersecurity can only be performed legally under the sovereignty of national government.
This isn’t to say that there aren’t very real concerns/drawbacks to such a decision, however. Besides any ethical/moral quandries about engaging the military on principle, there are very real limiting factors on your individual freedoms while on active duty; service members are first-and-foremost beholden to orders and matters of national security larger than themselves. Consequentially, most people who join the military incur a radically altered lifestyle compared to the greater general population, often in ways they could not expect before joining. Lastly, compensation is likewise generally not comparable to the similar work performed in the commercial sector.
Cyber-adjacent employment
Another common in-road into cybersecurity is through working in roles related to - but not directly involved with - cybersecurity itself. Oftentimes, these are technical roles such as systems administration, software engineering, IT helpdesk, etc. Through working in these roles and developing your competencies in the fundamental technologies cybersecurity professionals help secure, you create a relevant work history to pivot off of. Alternatively, you may seek out security-centric functional tasks within your current employer; in this way, you progressively shape your work accomplishments to contain more cybersecurity-related contexts.
While this approach doesn’t innately require a degree or military service, it’s not without its own risks and issues. Oftentimes, you’ll need to spend years in jobs (likely multiple jobs) not performing cybersecurity functions in cultivating your work history. You’ll likewise need to find other facets to promote your employability such as projects, volunteer work, published research, etc. Oftentimes, people adopt this approach in conjunction with the University approach described earlier; if you can’t and do not already possess a pertinent degree (or a degree of any kind), you can reasonably expect this road to take much longer.
“What about bootcamps?” Cybersecurity bootcamps, which offer intensive multi-week (or even multi-month) trainings at a fraction of the cost of a degree have a mixed track record. Based on student reviews, a lack of data transparency, and other reported issues, I am not comfortable with endorsing this route as a consistently viable approach. However, the number of folks that have successfully entered the workforce through one is non-zero, so your experience may vary.
Exploring Career Paths
Only %13 to %16 of all U.S. commercial cybersecurity openings are involved in what is classically considered “hacking”.
Most people from the onset envision a career in cybersecurity as being akin to a cinematic hacker, compromising computers, phones, mainframes, etc. On the contrary, per data collected by Cyberseek, the vast majority of cybersecurity job openings are not directly affiliated with that kind of work. Only %13 to %16 of all U.S. commercial cybersecurity openings are involved in what is classically considered “hacking”.
The above numbers were derived by determining the total number of roles affiliated with Task Description T0028: “Conduct and/or support authorized penetration testing on enterprise network assets” (Exploitation Analysts & Vulnerability Assessment Analysts) and dividing them by the total number of openings. Because Cyberseek denotes that any single opening may fit multiple categories, the %13 to %16 reflects minimal and maximal overlap between the two.
Cybersecurity is both blessed and cursed in being a very large tent for many different professionals to setup shop under. If you think you’re interested in cybersecurity, it’s worth exploring the particular career trajectories out there and what they do.
There are less technical roles such as…
- Governance, Risk, and Compliance (GRC) functionaries
- Lawers
- Project Management
- Teaching
- Insurance underwriting
And there are more technical roles, such as…
- Incident response
- Penetration testing
- Security engineering/architecture
- Malware analysis
- Application Security
Knowing more about what kinds of work exists in cybersecurity will help inform you of what your next steps might look like; moreover, your interests may (and likely will) change over time, so learning more about the breadth that the industry can provide is useful before pivoting. Some responsibilities in cybersecurity can seem really abstract, so it can be grounding to know the answer to “what does [role] actually do in their day-to-day?”
Below are some example resources that you can look into to get a better idea of both the breadth and depth of work that exists:
- The Haunted Hacker podcast features 1-on-1 interviews with various figures from across the industry. While the episodes could benefit from some editing (they are just the raw audio), the number and types of guests to appear make for a good survey of the field.
- SANS has assembled a list summarizing some of the types of work various positions perform.
- The Cybersecurity Career Master Plan is a book you can use to read-up on various career options (and how to grow your career into its next steps).
- The Cyber Work podcast has various episodes labeled “What does a [job title] do?”, mostly 1-on-1 interviews with people who work their respective roles.
Improving your employability
Once you’ve decided you want to work in cybersecurity, come up with a plan on developing your foundational concepts, and identified what specifically you want to do professionally, the last (and ongoing) step is improving your employability.
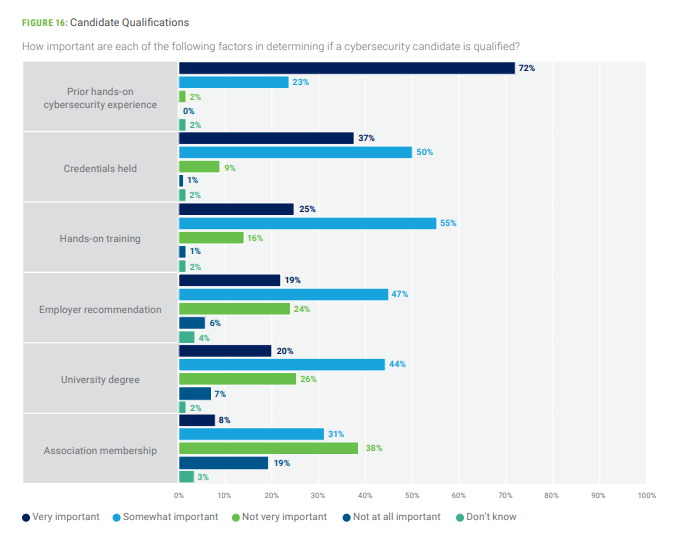
According to ISACA’s State of Cybersecurity 2023 survey report, hiring managers prioritize the following factors among qualified applicants:
The above results have held relatively unchanged year-over-year with employers consistently prioritizing:
- A relevant work history
- Pertinent certifications
- Formal education
- Everything else
With each step down, the impact of said factor drops off considerably. For example, 1 year of university is not nearly as impactful as 1 year of working experience in the field. It’s important to be mindful of how much time, energy, and money you allocate to each line of effort vs. how much return on your investment can be expected.
Actions to improve your employability may include:
Continue to leverage free resources to hone your craft or acquire new skills.
Pursue in-demand certifications to improve your employability.
Foster a professional network via jobs listings sites and in-person conferences.
Take note of the feedback you receive in interviews and adjust your efforts accordingly.
Pursue cyber-adjacent employment (if not cyber employment more closely aligned to your desired endstate).
Pursue a degree-granting program (and internship experience while holding a student status).
Get constructive feedback on your resume’s formatting.
Apply your skills into some projects in order to demonstrate your expertise.
Next Steps
Interested in leaping immediately into getting your hands dirty and exploring cybersecurity training?